The recent Microsoft data breaches reveal why end-to-end encryption is so important
There have been a few documented leaks and breaches of data at Microsoft in the past year:
- October 2022: Sensitive Data of 65,000+ Entities in 111 Countries Leaked Due to a Single Misconfigured Data Bucket
- July 2023: Chinese Hackers Breached US Government Email Accounts, Microsoft Says
- September 2023: 60,000 Emails Were Stolen From 10 US State Department Accounts
More details here: Microsoft Data Breaches: Full Timeline Through 2023
The lesson we keep learning over and over in the tech industry is: even a corporation as large and as trustworthy as Microsoft will make mistakes. Corporations are run by people, and people make mistakes. Attackers are highly motivated and sometimes even have large financial backing.
Centrally storing customer data in the clear is always a risk – if there is a breach, then it affects every customer. Even though the leaked and stolen data was very likely encrypted in transit and at rest, that didn’t prevent Microsoft’s first-party systems from reading and processing that data because Microsoft controlled the encryption keys, which is why it didn’t prevent the attackers who got into those first-party systems from also accessing that data.
End-to-end encryption makes it incredibly difficult for a mass data leak to happen because the encryption keys aren’t controlled by a central entity. Each user’s devices manage the encryption keys for them. If someone were to gain access to a service’s internal systems, they wouldn’t be able to read any of the customer data because it was encrypted with keys the service doesn’t control. If someone were to breach a specific customer’s device, others customers’ data not present on that device wouldn’t also be leaked. Again, when using end-to-end encryption, data is encrypted in isolation entirely on each customer’s devices before being sent to the cloud, dramatically reducing the risk and scope of a data breach.
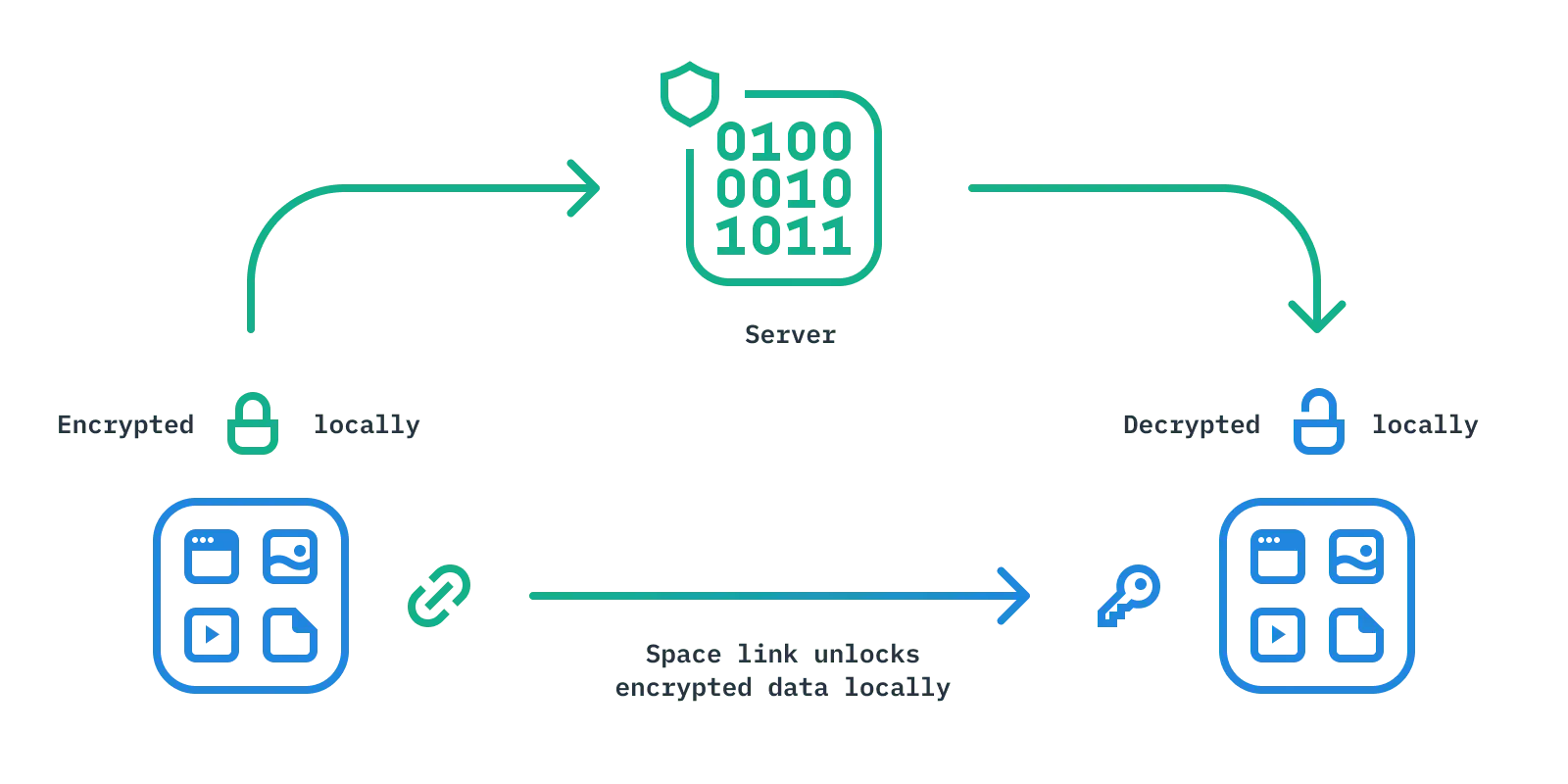
We’ve been focused on end-to-end encryption and privacy preserving practices from day 1 at Shareup when building new.space – it’s important to us to protect our customers as best we can. Everything added to new.space is encrypted on your device before being sent to our service. It’s then decrypted on each destination device that joins the space through the secure invite link. We at Shareup never have access to encryption keys for your data.
The next time you use new.space, pay attention to how fast items you add to a space show up in the space opened on a different browser. Amazingly, all those docs, photos, and bookmarks showing up so quickly were fully encrypted, transmitted, and then decrypted ⚡️ Security and privacy doesn’t have to be inconvenient or difficult 💪
We’ve written up an End-to-end Encryption FAQ here, check it out. And I’ve collected all of the articles mentioned here, along with a few additional resources, here in this read-only space:
And if you have any questions about E2EE, privacy, or new.space in general, then join us over at shareup.world as we work to make new.space even better.
